- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Why the Mitre Engenuity ATT&CK Evaluations Matter for CISOs

This year’s MITRE Engenuity™ ATT&CK Evaluation simulates techniques associated with notorious threat groups Wizard Spider and Sandworm to test solutions’ ability to detect and stop APT and Targeted Attacks.
Read time: ( words)
As the cyber attack surface continues to rapidly expand, enterprises need a security solution that can help organizations to better understand, communicate, and mitigate cyber risk across their entire IT ecosystem. And with many offerings on the market, choosing the right product can be challenging. CISOs can make a more informed decision by leveraging the MITRE Engenuity ATT&CK Evaluations and framework to evaluate the efficiency and effectiveness of market-leading security solutions.
What is the MITRE Engenuity ATT&CK Evaluation?
By aligning to the MITRE ATT&CK framework, the MITRE Engenuity evaluation provides a complete story of the attack by testing a solution’s ability to detect an adversary performing a targeted attack. Evaluations conducted by MITRE Engenuity do not generate any rankings or ratings. This means that, unlike traditional testing, MITRE Engenuity is solely focused on the product’s protection efficacy and detection capabilities after a compromise has occurred.
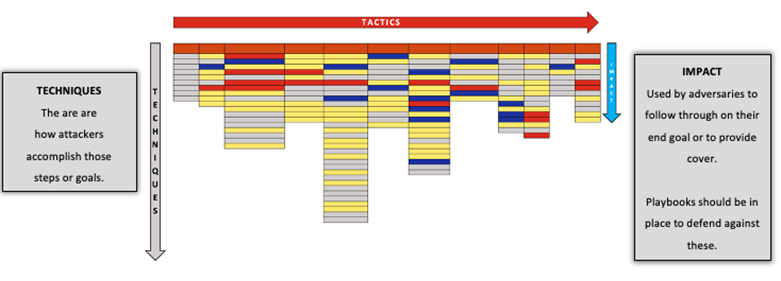
Figure 1: Wizard Spider and Sandworm evaluation, 180 ATT&CK techniques across 12 ATT&CK tactics are in scope for this evaluation.
The MITRE ATT&CK framework is a valuable tool that helps the cybersecurity industry define and standardize how to interpret an attacker’s approach and provide a common language to describe threat group behaviours.
2022 MITRE Engenuity Overview
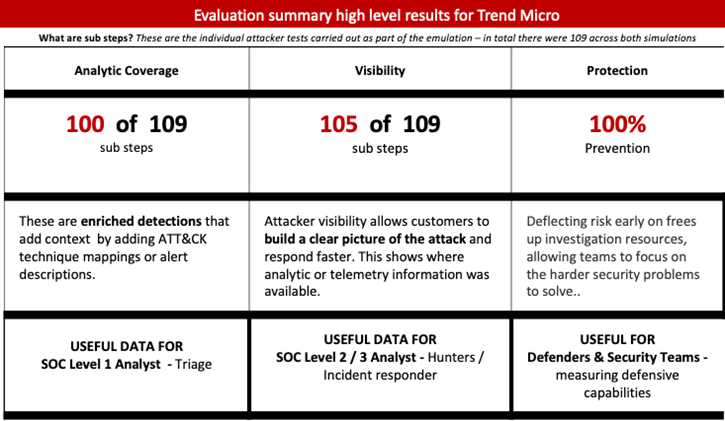
In this year’s evaluation, MITRE Engenuity emulated Wizard Spider and Sandworm tradecraft operational flows, simulating the behavior used in the wild by these notorious groups. Over the two scenarios, 109 attacker steps were executed.
Similar to the previous year, Trend Micro’s cybersecurity platform showed impressive results.
Leveraging the evaluations and framework
CISOs can leverage the MITRE ATT&CK framework to tell a complete story that helps simplify security communication across their organization, provide complete coverage visibility, and assess for gaps to discover where they may be vulnerable to threats. Increased visibility also helps you determine any coverage overlaps, enabling you to optimize costs. After you’ve identified your security needs, you can use the evaluations to compare vendors and determine which solutions are best suited to fill this gap.
- When evaluating the performance of vendors, it is important to consider the hierarchy of detection types. There are 5 types identified by MITRE ATT&CK:
None: While no detection information is given, it doesn’t mean that no detection occurred. Rather, it means it did not meet the required detection criteria set by MITRE Engenuity. - Telemetry: Data was processed that shows an event occurred related to the process being detected.
- General: A general detection indicates that something was deemed suspicious, but it was not assigned to a specific tactic or technique.
- Tactic: A detection on tactic means the detection can be attributed to a tactical goal (e.g. credential access).
- Technique: A detection on technique means the detection can be attributed to a specific adversarial action (e.g. credential dumping).
Seeing the full security picture
Trend Micro Vision One™ with industry-leading EDR and XDR capabilities is part of our unified cybersecurity platform, which helps organizations better understand, communicate, and mitigate cyber risk across their entire attack surface. More visibility helps connect the dots of the attack surface lifecycle, minimizing alert fatigue for security teams and allowing them to focus on critical attacks.
Learn more about the evaluation and attack techniques used on our MITRE Engenuity ATT&CK resource page.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

